Malware Analysis
At Right Turn Security, we take a structured approach to protect businesses from malware attacks. Malware exhibits different behaviors within networks, and our team is highly trained in behavior analysis to detect and eliminate hidden threats within an organization’s infrastructure.
Collect
We initiate the malware analysis process using advanced sample collection techniques tailored to detect malware behavior patterns.
Analyze
Our malware specialists conduct in-depth analysis using cutting-edge technologies based in the UK to uncover hidden threats.
Response
We provide a detailed report outlining the malware’s lifecycle, behavior, and impact, along with actionable recommendations for mitigation.

Malware Analysis Training
- Syllabus based on MSAB
- UK Certified Trainers
- Job Training
- UK Law Based Court Room Skills
- Professional Report Writing
Malware Analysis Tools
- Wireshark: It is a network analyser tool which analysis the network traffic linked with the system.
- Reg Shot: This tool analysis the changes happened in the registry and files of the target system.
- IDA Pro: This tool is an interactive disassembler and debugger used to analyse and understand the code with the help of different security plugins.
- Sys Tracer: This tool helps to track registry changes in a target computer.
- PEID: This tool is used to detect PE Packers, cryptors and compilers found in executable files.
- MitecEXE explorer: This tool helps to get information regarding executable files such as version info, sections, classes, packages and directories.
- DNS Sniffer: This network sniffer tool basically shows the DNS queries sent on the system.
- Dependency walker: This tool helps to scan any 32bit or 64bit windows module (exe, dll, ocx, sys) and builds a hierarchical tree diagram of all dependent.
Basic Malware Analysis Example
Your friend has already opened the document attachment. What happened? Is his machine already infected? Find proof for/Argue your answer!
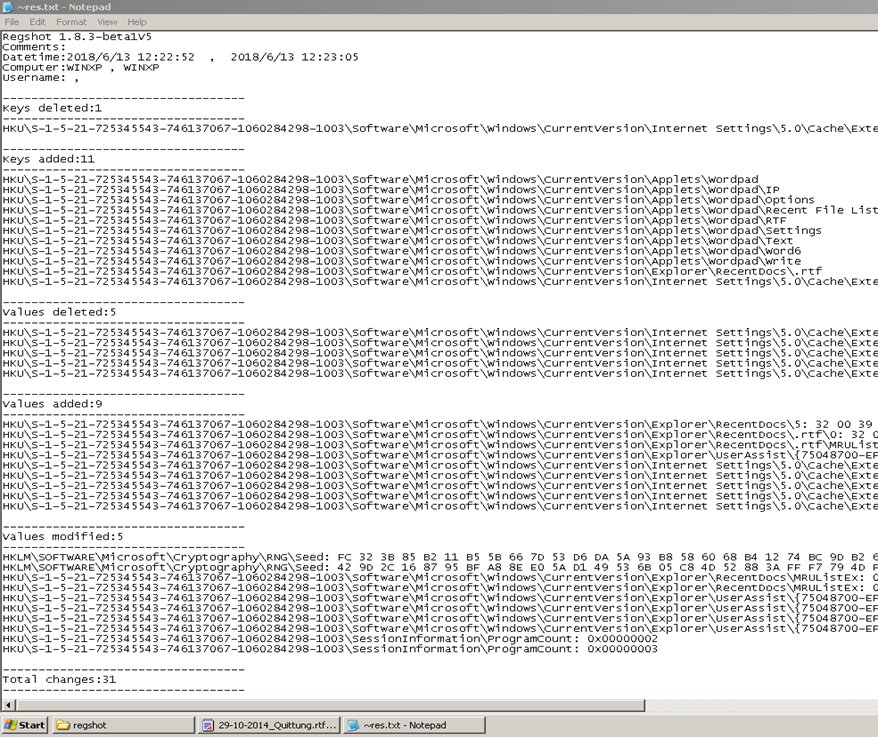
To find out changes in the machine, reg shot has been used. We compare two shots. One is taken before opening the document and second shot is taken after opening the document. The comparison report shows 31 changes, which are related to normal functioning of system. No infected values are found. This proves that the system is not infected by just opening the document attachment. My friend opened the .rtf file which will not affect the system. The system can be infected by double clicking on the image file. Regshot comparison report proves that machine is not infected. Figure 2 shows the comparison report.