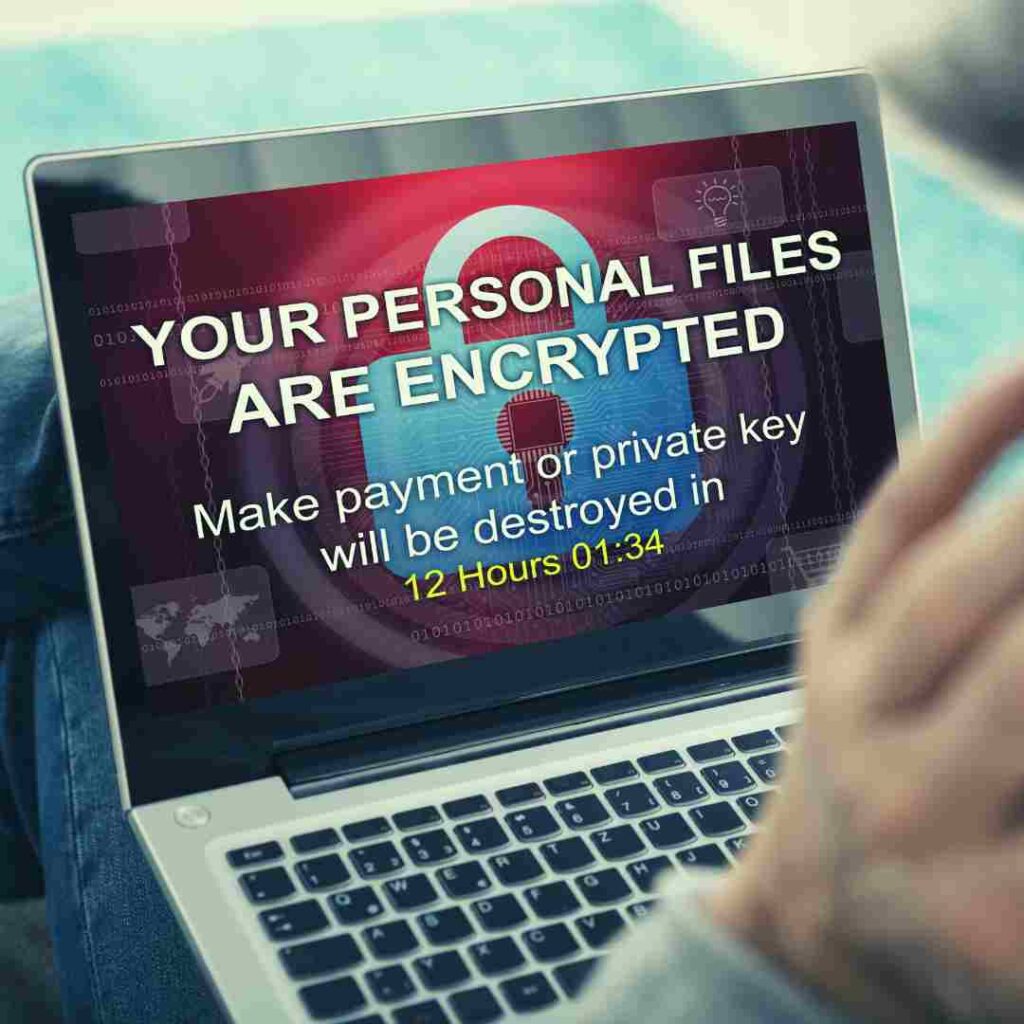
Best Cyber Security Services
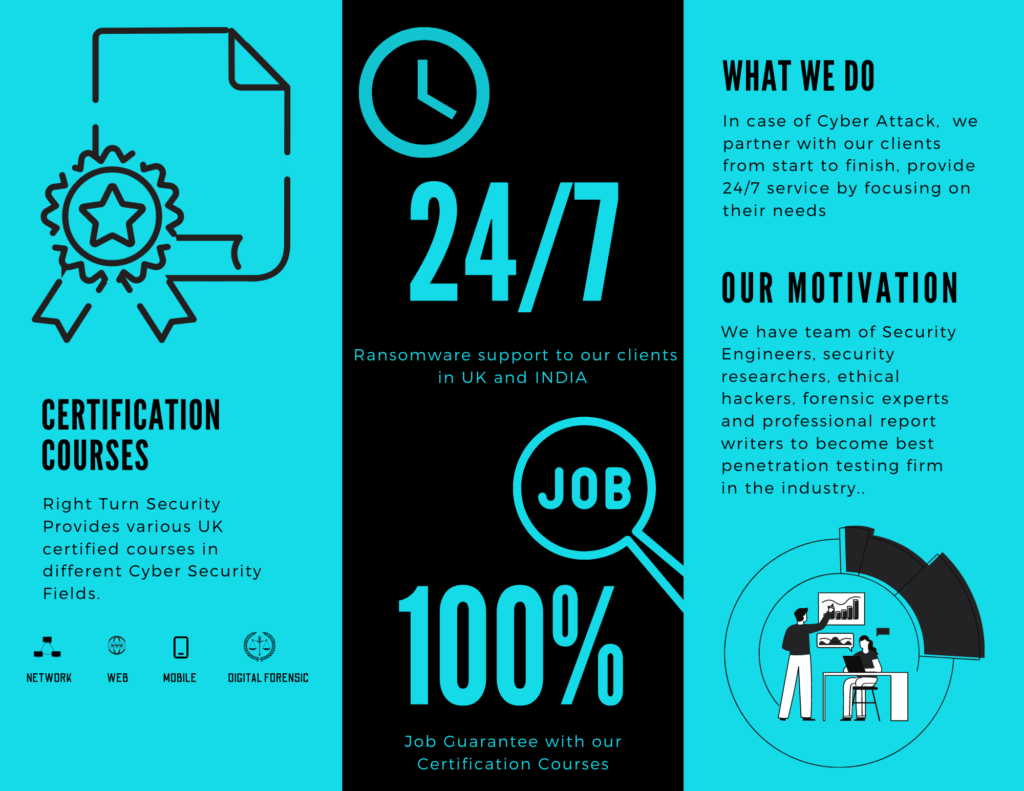
Right turn Security provides best cyber security services in all around world. The company is based in UK and India. The company professional are highly experinced in their domains. We are covering all the domain of cyber security. Organisation can contact us for securing their network and web interface. We can also respond to the incidents arise in the case of cyber attacks. We also provide training to the employees working in the organisations. We are directly dealing all of the below services.
Our Testing Methodology
The methodology used by RT Security is based on discovering, analysing, documenting and exposing target’s area of risk. This methodology is suitable for performing penetration testing on website. It is described in 6 steps. Following are the phases of methodology :
This process will cover all the logistical, network and administrative data about the target. It also includes various database version, software version, hardware used and various third-party plugins.
This phase will analyse the discovered data found in discovery state. This phase will aid to discover the security weakness in the host.
In this phase, penetration testing will be performed to probe for areas of weakness. Different techniques will be used to exploit the vulnerability.
This section helps to analyse the risks posted by attack simulation state. This stage will also analyse the impacts of the vulnerabilities exploited.
Complete documentation of the vulnerabilities will be finished after analysis process.
In the end, a detailed report will be generated for preventing found vulnerabilities by different techniques and solutions.
Major Testing Techniques
This testing technique will verify some mechanism of account suspension is available and is working correctly.
Testing will be performed on input fields which are directly connected to database. Verify the coding behind the HTTP request and response procedure.
Testing will check session cookie scope, duration, session expiry technique and session termination process.
It will include checking for error code, to ensure error messages not contain any critical information. Further testing will also be performed to check for stack traces
This part will cover all the authorisation and authentication testing. It will include testing for path traversal, missing authorization and access control problems in host.